Abusing DNS in my homelab
Scenario:
Today we will be targeting my home lab to demonstrate how the regular functionality of DNS can be abused. In this scenario we will be assuming that an attacker has gained foothold on a victim network by stealing their Wi-Fi password via a social engineering attack. We will demonstrate the complete steps an attacker would take to compromise a Pi-hole server and how they could use it as a means to steal user credentials.
Tools Used:
- Kali Linux
- Burp Suite
- Gobuster
- Hydra
- Social Engineering Toolkit
Information Gathering
Using the ifconfig command we can see that we are automatically given the IP of 10.1.1.96. The fact that we have been automatically been assigned an IP means that DHCP is being used to distribute IP addresses and other information.
What is DHCP?
Dynamic Host Configuration Protocol is a network protocol used to assign IP addresses when devices connect to a network. Clients initially make a broadcast request to discover any DHCP servers on the network, the DHCP Server then responds offering the client an address along with other information such as the subnet mask and DNS Server addresses.
It can sometimes be useful to take a closer look at DHCP server offerings. The nmap scripting engine can be used to manually send out a DHCP discovery broadcast and report back with its findings.
sudo nmap --script broadcast-dhcp-discoverThis is interesting, most home networks use the default gateway (router) as the advertised DNS server as it is typically the default configuration. In this case we can see that 10.1.1.232 is the advertised DNS server.
We can confirm this by performing an nslookup of google.com
nslookup google.comWhat is DNS?
Domain Name System (DNS) converts domain names into IP addresses. In the above image we can see DNS in action, when performing an nslookup we ask the DNS server to perform a lookup to translate a domain name to an IP address. In this case it determines that google.com is actually 142.251.215.238. If you stick this IP address into a browser it will take you to the Google homepage page you are familiar with seeing. DNS makes it much simpler to browse the internet as we simply need to remember a domain name rather than its associated IP.
Enumerating the DNS server with nmap
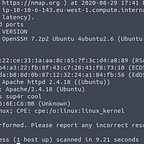
sudo nmap -A 10.1.1.232 -oN dns_scan.txtFrom the nmap output we discover that 10.1.1.232 is actually an Ubuntu server running Pi-Hole.
What is Pi-Hole?
Pi-Hole functions somewhat like a firewall. It is capable of receiving DNS requests, comparing it with a blacklist and determining whether it should allow or deny the forwarding of a given DNS request. This is mostly used to block advertisements on home networks, however it has additional functionality that makes it an interesting and powerful target for attackers which we will explore later.
It also looks like there is a web server running on port 80, we should poke at this to see if we can identify any attack vectors. Navigating to http://10.1.1.232 we find the default homepage for the Lighttpd server package.
This default page isn’t much use to us, we should determine whether there are any interesting files/directories on this web server. To accomplish further enumeration we will use a file/directory bruteforcing tool named Gobuster. Gobuster is an open source tool which takes a dictionary file as input to enumerate any interesting paths on the web server it does this by appending each line in the dictionary file to an HTTP request, monitoring it’s response to see whether any is valid.
gobuster dir -u http://10.1.1.232 -w /usr/share/wordlists/dirb/common.txt -o gobuster80.txtGobuster Discovers /admin which redirects to http://10.1.1.232/admin/login.php. Navigating there we are presented with the Pi-hole login page.
Password Attack
Notice that there is no username field. This makes it considerably easier to attack as we only need to figure out the password rather than a username/password combination required by most web pages. We can attempt to determine this password with Hydra.
About Hydra
Hydra is an open source password-cracking tool used by ethical and malicious hackers to conduct password attacks against various authentication protocols. Hydra like gobuster can take a dictionary file as input and run each line against an authentication mechanism. In this case we will be using it’s HTTP functionality to try each password in a file to see if we get any hits.
Hydra requires a bit of information about the authentication process, we will need a way to obtain the following:
- HTTP Method: HTTP supports a variety of methods like GET,POST,PUT and more. In many cases POST is used for authentication.
- Directory path: We already know this thanks to gobuster /admin/login.php
- IP address which we already know
- Password or wordlist
- Username, in this case it will be empty as there is no username required for authentication
- A method of determining failed attempts which is, in most cases a string like ‘incorrect password’
A simple way of getting deep insight into HTTP requests is to insert a proxy in between the communications of a client and server. In this case we will use Burp Suite to accomplish this.
About Burp Suite
Burp Suite is a powerful tool used to test web applications. It can act as a proxy server, intercepting HTTP/HTTPS requests for deeper examinations into how a web application functions.
First we need to configure our browser to send all HTTP requests to Burp Suite. To accomplish this we will use a plugin called foxyproxy. Burp Suite by default runs on localhost on port 8080 so we need to add this to the foxyproxy config:
We enable the proxy intercept functionality and attempt to authenticate to the web application. Below we can see what Burp Suite captures.
The last thing we need from Burp Suite is to determine how the web application responds when an incorrect password is entered. Hydra will need this to determine when a login succeeds. We can figure this out by moving our request to the repeater tab and examining the response the web server returns upon entering our bogus password.
The server responds with “Wrong password!”.
With this we now have all the prerequisite information required to perform the password attack:
hydra 10.1.1.232 http-form-post "/admin/login.php:pw=^PASS^:Wrong password" -l "" -P /usr/share/seclists/Passwords/xato-net-10-million-passwords-100.txt -vV -f Boom we get the password to login!
Now that we have access to the admin panel of the Pi-hole we can explore the some of the features and functionality that makes it such an appealing target for hackers. One such feature is the ability to look at log files (in real time!) to see what websites users are visiting throughout the network.
Looking at tail.log we can see DNS requests to resolve various dell domains from 10.1.1.45.
DNS Abuse
How can we use this information to our advantage? One attack we can look at performing is DNS poisoning.
What is DNS Poisoning?
DNS Poisoning is an attack where an attacker modifies a DNS record to point a user to an alternate, often malicious website. In the nslookup example earlier we saw that google.com resolved to 142.251.215.238. In a DNS Poisoning attack we can modify a DNS record to instead have the domain google.com point to our IP at 10.1.1.96. With a proper set-up the user will have few clues to determine that they are not on the legitimate website.
In this case we know the user at 10.1.1.45 is regularly visiting dell.com. We can use this to our advantage by using a tool called the Social-Engineering Toolkit (SET) to clone the dell.com login portal. We then use our credentials on the Pi-hole to point the dell.com domain to our attacker’s IP at 10.1.1.96. When the victim next attempts to authenticate to dell.com, their credentials will be sent to our attackers machine.
Lets first setup the Social-Engineering Toolkit, selecting the Credential Harvester Attack Method. We will need to clone the Dell authentication portal to conduct the attack
Configuring SET:
we can confirm the the login portal is working by navigating to http://localhost
Now all there is left to do is to use the Pi hole to redirect DNS queries from dell.com to our attacking machine:
Boom we get the username/password from the victim@10.1.1.45
What can we learn from this attack?
Pi-Holes are a useful technology, they allow ad blocking at a network level. This is mostly fine on protected internal networks such as the one we examined today. You may however be surprised to learn that there are many publicly exposed Pi-Hole servers available on the internet today. We can use Shodan to find these publicly available servers like the one shown below:
If a DNS server (or any device capable of modifying DNS records) is compromised it does not matter how strong your passwords are, they will be at risk of being stolen by a determined hacker.
How can you protect yourself from this attack?
Do not publicaly expose Pi-Hole’s to the internet. It does not matter how strong your passwords are, with enough time and computational power an attacker will eventually determine your credentials. Note that this also includes your home router, as they are often capable of modifying local DNS caches.
Use multi-factor authentication. Multi-factor authentication does not trust any one factor to authenticate, if dell.com uses MFA then the attacker will still be unable to login to the service. Although with enough effort by the attacker, this too may be defeated.
Remain vigilant. In this setup SET did not use HTTPS meaning that the webpage presented to the victim was an HTTP page. This can be observed by the lock icon present on most browsers. If this lock icon is not visible when authenticating to a page on the internet, you should avoid providing any credentials. If you suspect fowl play you can use nslookup and compare the DNS response to that of a public DNS server like Google’s (8.8.8.8).