Safe self-custody, how to do it?
FTX has proved one more time that when you have something to lose in crypto, self-custody is a must to sleep well at night. But how to do that safely?

The FTX and Alameda debacle has proven to us once again that there is no safer solution than self-custody. And while we have seen multiple calls for it over the past two weeks, it is important to note that self-custody isn’t simple. If you’re asking yourself how to do it safely, you came to the right article.
TLDR
- Not your keys, not your coins. Let’s never forget that.
- Centralization isn’t just a buzzword. Look at this $400m+ of forever frozen USDT, your wallet could be next.
- Transparent and diligent proof of assets is a must. Remember Terra with an $18B market cap but tiny liquidity and backing?
There’s a great number of articles written on the topic of centralization and risks in crypto. So, instead of writing another general and abstract article, I’ll share my personal experience instead.
Avoid centralized exchanges

First of all, avoid centralized exchanges at all costs, this is one of my mottos. In 2017 I deposited a few ETH to a famous and popular centralized exchange but I was never able to get these assets back, even after wasting countless days and nerves fighting with their customer support. In other words, I got scammed by a tier 1 exchange. This was long before the FTX debacle. So, if we cannot trust any tier 1 exchange, do you really think we can trust tier 2 and tier 3 exchanges?
The best and most straightforward way to avoid losing your funds on centralized services and to be able to sleep well every single night — is to avoid using them and self-custody all your funds.
What DeFi protocols to use?
You have many complex financial tools outside of centralized exchanges.
- Where to exchange coins? 1inch is your friend.
- Trade with leverage? dYdX
- Yield farming? Yearn
- Leveraged yield farming? Gearbox.
There’s only one piece missing to achieve the complete CEX experience — decentralized on/off ramps. I personally don’t know why anyone hasn’t solved this problem yet. But meanwhile, an alternative you can use is Binance P2P. It’s p2p on/off ramp but, being from Binance, you should have an account there which is its biggest point of failure.
Not your keys — not your crypto
This is not only a meme but a good call to action. In a nutshell, a private key is just a big number that only you should know. Knowledge of this number IS the ownership of funds.
This is what I do to sleep well:
I have three wallets.
Cold Wallet

I use ledger nano, where I keep important sums of money. I can not afford to lose it.
Hot wallet
Metatask — where I buy random tokens and interact with DEXes etc. If I need to do an operation with tokens from a cold wallet — I transfer them to a hot wallet first, and I do everything using it before sending tokens back to my cold wallet. The aim is to minimize the start-contract approvals I do from my cold wallet.
I haven’t tried Ambire wallet myself yet — but we like what they are building and they are our protocol friends. It is a smart contract wallet that you can check out here.

Public wallet
One that has .eth name for it, lens address, and has good “credit history” — I don’t do <redacted> things from this address. I use it for hackathons to claim POAPs and don’t dump DAO airdrops. The reason is, I believe that as time passes, and, the more the crypto space matures — the more important on-chain history will become, aka on-chain credit score. I keep here only sums of money that I want the public to know and don’t do any trading.
Private key backups
There are a bazillion tutorials on the internet of how to back private keys. What do I personally do?
1) I split keys (24 words) into left and right halves
2) I write all the places where I can possibly store the “halves” of keys: smartphone, metal plates, hidden postcards, inside of a plush toy, in my in-law's garage, etc. While outlining several properties:
How likely this storage a) can be lost or broken, (e.g: I can forget about it)? . Any electrical device can break. b) be compromised, (e.g: someone else will have access to it), for example when you cross the UK border — you can be legally obligated to unlock your phone
My rule of thumb is to follow the 2FA philosophy: something I have + something I know + 3 place redundancy.
How to safely use dApps
I usually interact with web3 decentralized applications only by using my hot wallet. In case of an emergency, my cold wallet stays safe. It doesn’t have any erc20 approvals, dApps interaction, etc.
When I interact with a smart contract, the first thing is to verify that the address of the dApp URL is legit. I google the “protocol name + Twitter”, and check if their Twitter account has among its followers, people I follow myself, such as crypto influencers, friends, and experts — it is a way for me to verify if a project is fake or not, and they also have the link for the dApp or website on their socials.
When you start using a dApp, you notice that every app asks for erc20 approval first. I never do infinite approvals, if a dApp tries to do an infinite approval without offering the limit as an option — that’s a signal to be very careful. Metamask gives an option to manually change the approval limit.
When signing the actual DeFi operation, for the first time I just copy-paste the address in Etherscan and see what’s there. If the contract is not verified — it’s a huge red flag, run away. If verified — I check how many other transactions happened with this contract, and what were these interactions. I also check the comment section on etherscan, in case of a bad experience or scam — people usually don’t hesitate to write warnings there.
After interacting with DeFi, it’s a good idea to visit Revoke cash and see what contacts you gave allowance to, in other words, the ability to take your money. It’s a good idea to cancel approvals for upgradable contacts, even for reputable protocols.
For the different chains, I set different google chrome profiles. For different profiles, I choose a different background color that corresponds to the chain: red for Avalanche, purple for polygon, etc.
For my testnet wallet — I use a different browser, Brave with Metamask (Brave’s default wallet is not good enough).
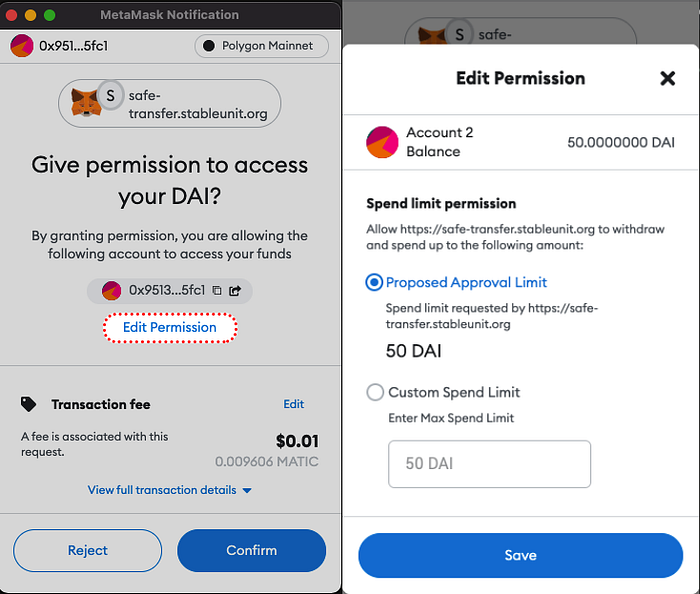
For transferring any sizeable amount of money to real people, I use SafeTransfer.
We developed this tool during a hackathon (that won a nomination from gnosis safe) after I had two cases where I accidentally sent thousands of dollars on the wrong blockchain and I didn’t want to repeat this mistake. SafeTransfer really makes it stress-free when I need to send money to anyone, especially when it comes to tens of thousands. It also works with gnosis-safe, try it out.

Ledger wallets can work with Metamask. However in my case when I work with gnosis safe- it works with Firefox only, I don’t know why. Be sure you read the address of the contract with which you interact. Also, Ledger nano has a cool feature of having a hidden account: you set a second pin for a secret account, in case of an emergency.
On my smartphone, I use Metamask and Trust Wallet. 1inch has also a great wallet. Coinomi and Jaxx are outdated, I don’t recommend them.
What I found peculiar, power users at Devcon hesitated to claim POAPs on the spot and rather took pictures to claim them later. They didn’t do so for security reasons, so malicious actors wouldn’t know where they are. I found it to be a good practice.
Centralized assets.
Another flavor of centralization comes in the form of assets themselves. Did you know that even on the most secure cold wallets such as Ngrave, USDT and USDC can just seize your money at any moment? Despite you controlling your keys — the token itself has a backdoor (line 341). If you think it’s obvious — you would be surprised how many people don’t know that.
That argument that many of these blacklisted accounts belong to criminals and hackers is faulty. Remember trackers in Canada and how the government just froze their bank accounts and left them without money to survive?
Now it will become easier than ever with centralized stablecoins. You can’t imagine how easy it will be with CBDC (Central Bank Digital Currency) — it would be a totalitarian nightmare straight out of the Orwellian 1984.
You don’t agree with the government? Any corrupted three-letter agency employee can starve you to death with a single crypto signature. Gladly, we’re not there yet, but OFAC is coming and it costs them close to nothing to force Circle (the company behind USDC) to require KYC for all users.
What’s the solution?
The best of all is to use pure Bitcoin and Ether — these assets had proven to be extremely reliable and they were never technically compromised. At the moment of writing, there is valid concern about MEV censorship on Ethereum but for our needs this is not a critical issue. Because, even if 99% of blocks are censored — the uncensored txs will still pass, just at slower speed that is comparable to the typical bitcoin transaction.
But what if you don’t want to bet on the price of a volatile asset and still need a stablecoin? The first advice would be to keep only small and necessary amounts in USDT/USDC and swap the rest to DAI (https://makerdao.com/) or LUSD (https://www.liquity.org/).
They aren’t ideal: DAI’s collateral is mostly made of USDC and its derivatives, so Circle has full power to destroy DAI. Furthermore, if you have USDC — there are many other users of the system and you might consider the probability for your particular account to be seized is quite low. However, there’s only one collateral of DAI that everyone knows and that might pose an important counterparty risk. LUSD doesn’t have a USDC collateral issue, but it’s not that stable and often traded 3–4% above peg, it has huge exposure to ETH’s price and its 110% loans with 0% fee are not what they seem to be: you can be liquidated at way higher prices and pay for 0% the loan quite a sum during the origination process.
For that exact reason, I’m involved in Stable Unit’s development, it is still on testnet but design-wise the system doesn’t have any centralization issues, it has several levels of stabilization and safeguard above the MakarDAO model, to resist even severe market crashes, and, has a built-in saving account in every single coin. Consider checking it out and getting in the next batch of free NFT distribution.
Come meet us on Telegram or Discord, introduce yourself to the community and get to know them, the team, and Stable Unit.
For assets like wBTC, although it’s centralized overall by a group of several DeFi companies, the code of the token can’t blacklist individual accounts (line 94). If you want to have Bitcoin on Ethereum to use in DeFi then renBTC seems like a safer bet, although they have centralization issues that are set in place to prevent a possible economical attack on the system.
Proof of assets
As we all see, even multi-billion dollar reputable exchanges, with famous investors and connections, can still gamble their users’ assets. The seemingly different case of Terra has more in common than might appear at a very first glance: both of these projects didn’t have backing to support bank runs.
How do you avoid bank run problems? The simpler and most robust way — is to have all assets ready to be withdrawn at any moment and have rock-solid proof of it. So here, DeFi comes to play as the clear winner of transparency. Because of the nature of the open blockchain systems, there’s a very simple way to prove if a DeFi protocol has the assets they claim they have: simply visit a blockchain explorer such as https://etherscan.io/ and search for the protocol’s smart contact. This is an example of the curve 3 pool— it’s not that curve just claims it has the user’s liquidity, everyone can visit a blockchain explorer and verify.
What should be done here are two things:
1) Some DeFi protocols are complex, like Yearn. They use their liquidity in other protocols to gain yield, so the Etherscan verification can be quite complicated. In this case, it’s the protocol’s responsibility to show how anyone can independently verify the backing. I hope more and more people will demand such features. So, in the nearest future protocols that don’t have a clear way to prove assets — would be widely considered a red flag.
2) Be sure you understand the assets themselves. Market cap isn’t as important as actual liquidity.
Imagine a case: I can mint one coin A, sell it for $10, and mint another billion of them. The market cap of coin A would be $10B but that’s quite different from $10B of cash. In the same way, I can mint 100 million of token B, and create a liquidity pool of token A/B, so, even from a liquidity point of view, it would appear as a token with a billion-dollar market cap and 100m of liquidity!
But in reality, all of this would be backed by just $10. Do you think it’s a made-up example? check RootKit(I don’t even mention Terra here). So be sure you understand what is the real underlying liquidity of a protocol.
Another dimension of asset centralization risk is the underlying infrastructure. Be careful with Solana and Binance Smart Chain, since these blockchains are controlled by a few centralized organizations that can render any tokens/accounts on this chain — useless. Your friends here are L2s, like Optimism () or Arbitrum () and of course, Ethereum Mainnet itself.
I hope it was useful for you, if you like this blog post, consider following me on Twitter and feel free to ask any questions. You can join the Stable Unit socials here to learn more about what I’m working on.







